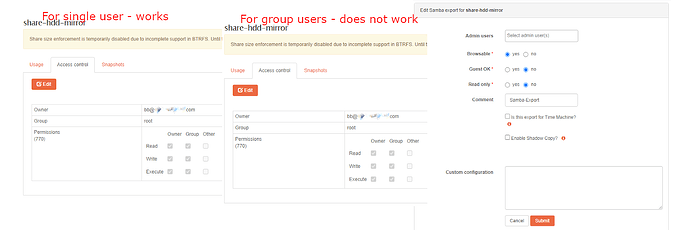
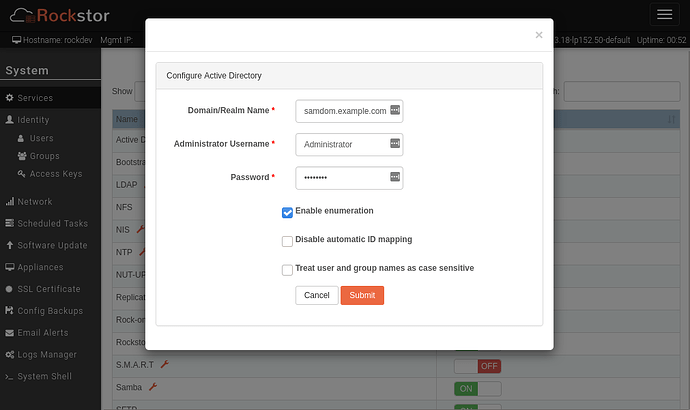
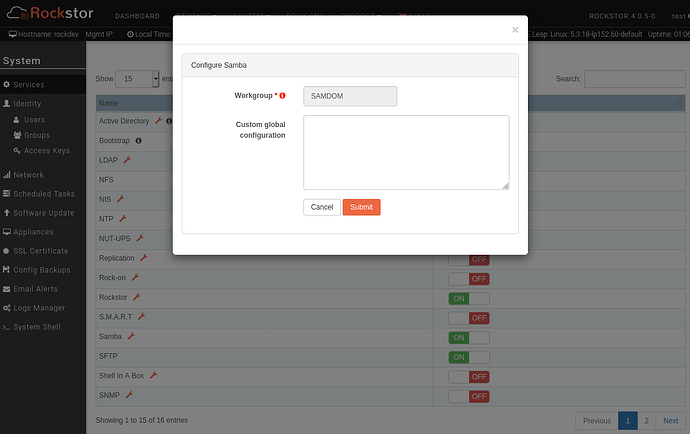
Hi @Flox,
thanks a lot for your feedback!
I already searched for idmap with samba, but I think, even after your explanation and additional research I am not sure, if I understand what it does or what it is important for.
I am not sure, what to use for the domain (EXAMPLE in your example**), because it was not clear, when to use the workgroup (I think its the NETBIOS name) and when the realm (what I generally mean when I refer to the domain name), but your link had some examples and at first I thought it was clear, but on second look I am still irritated.
They use EXAMPLE as name in the idmap configuration, but below they show the workgroup configuration
[global]
workgroup = EXAMPLE
realm = EXAMPLE.COM
security = ADS
kerberos method = secrets and keytab
Because workgroup does not contain the domain (for the Active Directory) I assumed, I have to put the same string there as in the workgroup definition.
In my case (of an Windows Server Active Directory) the NETBIOS name (as verified by nbtstat -n on an windows machine in the domain) and the domain are:
NETBIOS: FD
Domain/Active Directory: full-domain.com
(in fact in my example above I simply used domain, but everywhere where @domain was used there really is full-domain.com used).
I use full-domain.com to setup the Active Directory and put FD in the samba workgroup field.
But using FD for idmap definition somehow does not make sense to me: samba should look the defined ids up for the Active Directory, so for full-domain.com. Anyway - I tried both versions with dis-/enable samba and reboots in between and nothing changed anything in the share access.
Because of https://www.suse.com/support/kb/doc/?id=000017458#ad_examples I also tried both versions with backend type ad. This is what samba config looks like:
####BEGIN: Rockstor SAMBA GLOBAL CUSTOM####
idmap config * : backend = tdb
idmap config * : range = 10000-19999
idmap config fd : backend = ad
idmap config fd : range = 200000-2000200000
workgroup = FD
####END: Rockstor SAMBA GLOBAL CUSTOM####
Is ad or idmap_ad the module/plugin, that Rockstor uses?
You ask
A most likely unrelated note: do your user records on your AD server include a uidNumber and gidNumber ?
probably because of that passage:
Mappings must be provided in advance by the administrator by adding the uidNumber attributes for users and gidNumber attributes for groups in the AD. Winbind will only map users that have a uidNumber and whose primary group have a gidNumber attribute set. It is however recommended that all groups in use have gidNumber attributes assigned, otherwise they are not working.
(also from the link above)
I can not say for certain if that is set, but this is what the internet told me to check:
PS C:\Users\Administrator> Get-ADGroup -Identity "s_intern" -properties GIDNumber
DistinguishedName : CN=s_Intern,OU=SecurityGroups,OU=Groups,OU=FullDomain,DC=full-domain,DC=com
GroupCategory : Security
GroupScope : Global
Name : s_Intern
ObjectClass : group
ObjectGUID : b5b61c69-585d-4013-b89e-fexxxxxxxxx
SamAccountName : s_Intern
SID : S-1-5-21-639966690-3561479041-xxxxxxxxx-xxxx
PS C:\Users\Administrator> Get-ADUser -Identity "bb" -properties GIDNumber
DistinguishedName : CN=Benjamin Badel,OU=Office365_User,OU=User,OU=User,OU=FullDomain,DC=full-domain,DC=com
Enabled : True
GivenName : B
Name : B B
ObjectClass : user
ObjectGUID : ce83ccd1-4e0f-43a0-aa64-xxxxxb45xxxx
SamAccountName : bb
SID : S-1-5-21-639966690-3561479041-xxxxxxxxx-xxxx
Surname : B
UserPrincipalName : bb@full-domain.com
…and fields are not visible, so I would guess uidNumber and gidNumber are not set. But then again I found, that those ids are not required, when winbind is used in combination with samba (gidnumber im Active Directory | Mathom unfortunately in german).
You can test these settings above if you are game, but note that I’m unsure whether they pose a potential risk of altering your current AD server ; my apologies for my shortcomings here.
Is there really a risk of affecting the Active Directory (that runs on a different server under credentials not available to Rockstor)?
And please - no need to apologize, on the contrary: big thanks for the help so far!
**haha