Hi All,
I’m encountering similar issues as expressed toward the end of this message: Migrating from CentOS to OpenSUSE error with Users
I’m setting up a proof of concept/testing server (version 4.5.8-0 and fully zypper updated) and I’m encountering the following error when I enable the LDAP Service, connecting to an OpenLDAP server:
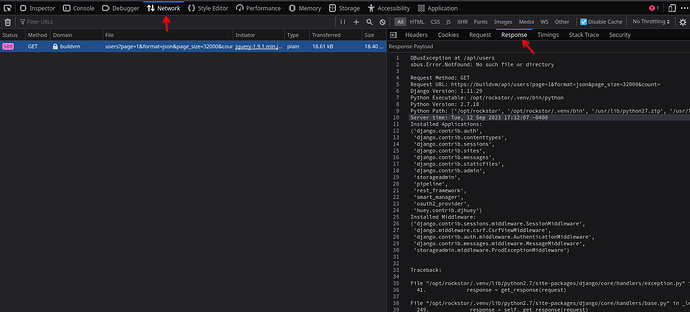
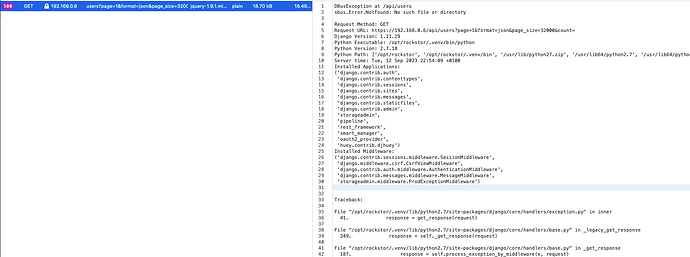
Unknown internal error doing a GET to /api/users?page=1&format=json&page_size=32000&count=
when I try to go to the Users page. Note: The Groups page works fine. Additionally, I get the same error when trying to edit a Share (clicking on the Share name in the list of Shares), or when trying to edit a Samba Share.
I believe I have the LDAP GUI settings correct. I can see all 14 of the LDAP users using getent passwd and the groups using getent group. I notice that LDAP based users/groups have an * rather than an x (like local users/groups) in the password space. But from what I read, that may just be because there isn’t any password information associated with them, yet.
I get the following information from the domain-status check:
sssctl domain-status ldap.mydomain.net
Online status: Online
Active servers:
LDAP: ldap.mydomain.net
Discovered LDAP servers:
- ldap.mydomain.net
While the connection seems active, I can’t login to the web interface with any LDAP user. I just receive “Login incorrect!”. (I’m not sure if an LDAP user is supposed to be able to login to the GUI or not.) There’s not a GUI based way for me to try and setup a share to be owned by an LDAP user, so I can’t test SMB access. In a shell session, I am able to “su” to the ldap users and get the correct response to “whoami”.
If I disable the LDAP Service, then the User page and Share pages work fine. It seems like there is some sort of problem with any page that needs to display a list of Users, whether it’s just a list, like the Users page, or a selection list, like in the Share-Access control tab.
I am happy to provide more information if needed, test possible solutions, or open a github issue on this, but wanted to check here first in case I’m just missing something that’s obvious to others.
Thanks!