As has been reported by a few users, our now legacy Rockstor 3 is now facing issues when trying to refresh the list of available Rock-ons.
SSLError: [SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed (_ssl.c:618)
After a bit of investigation, the issue appears related to older certificates used by the python requests package, which comes bundled with its own. Due to the age of these certificates in our legacy Rockstor 3 version, these certificates are no-longer valid, resulting in the error reported in the other forum thread linked above. Now that we know that, we can try to get around it.
Note that the following is a “hack” that should not be considered to be a solution. If successful, it will only allow to fetch the list of available Rock-ons but it will not resolve potential similar issues elsewhere that might arise. This issue is related to the older software used in Rockstor 3, an issue addressed in our Rockstor v4 effort along many other issues. As a result, the workaround detailed below should be considered as such and is provided as a temporary hack to help those who want to take the risk of a hack.
For those willing to give that a try, the call in question that is failing in this case is the following:
This is thus where we need to do some changes. As mentioned above, the problem here is that the python requests package uses its own CA bundle when making this request, which seems to have expired and is thus rejected. We can, however, force it to use the system’s CA bundle, which should then work fine. Note that there’s a second similar call that would need to be adjusted as well:
Now, let’s actually work around that:
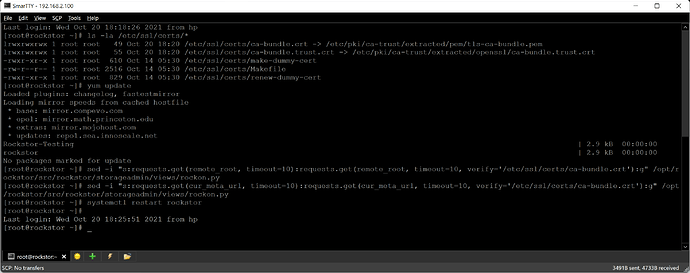
- run
yum updateand wait for all updates to be applied. You might even consider a reboot at this point if a lot of packages related to the core system were included. This is to ensure we have an up-to-date system, especially anything related to ssl certificates. - Locate your system certificates. By default, they should be located at
/etc/ssl/certs/. Make sure the following does list the certificates.
ls -la /etc/ssl/certs/*
- Now, we can tell python
requeststo use one of this certificates instead of its own. As mentioned above, we need to do this in two different lines of the same file:
sed -i "s:requests.get(remote_root, timeout=10):requests.get(remote_root, timeout=10, verify='/etc/ssl/certs/ca-bundle.crt'):g" /opt/rockstor/src/rockstor/storageadmin/views/rockon.py
sed -i "s:requests.get(cur_meta_url, timeout=10):requests.get(cur_meta_url, timeout=10, verify='/etc/ssl/certs/ca-bundle.crt'):g" /opt/rockstor/src/rockstor/storageadmin/views/rockon.py
for a quick info, the
sed -i "s:pattern:replacement:g" filecommand simply replaces inplace (-ioption) the characters that match a specific pattern (pattern) with a new string of characters (replacement).
Inspect the file to make sure have indeed added , verify='/etc/ssl/certs/ca-bundle.crt' to the requests. This will ensure the system’s certificates are used instead of requests’s default ones.
Finally, restart the rockstor service for the changes to take effect:
systemctl restart rockstor
You should now be able to go to Rockstor’s webUI, Rock-ons page, and click the “Update” button to get the list of available Rock-ons.