This is a wikified post documenting the implementation of Active Directory integration in Rockstor. It was done differently before version 3.8-9 using winbind as described here. This new approach uses sssd and is a much simpler and recommended one as per RHEL/CentOS documentation.
##User story and implementation summary
User should be able to add their Rockstor system to their Active Directory domain controller. We use realmd, which provides and simple way to discover and join Active Directory. Internally, realmd configures the System Security Services Daemon or SSSD to achieve this. Let’s dive into the UI and implementation details.
##Implementation detail
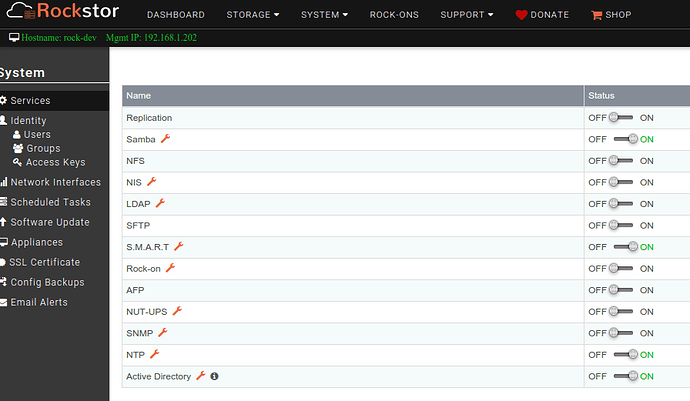
In the Web-UI, AD integration feature is available as one of the services under System → Services screen.
User clicks on the Wrench icon next to Active Directory and submit a simple form.
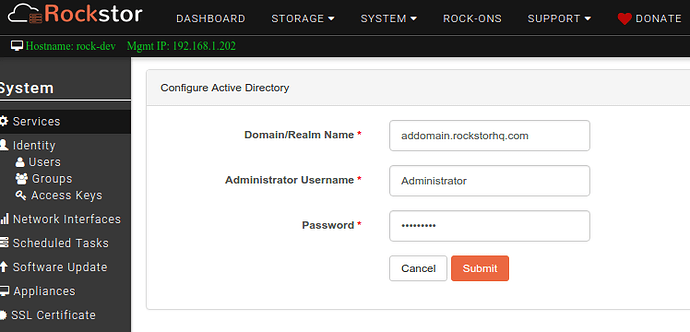
Following are the input fields with descriptions
- Domain/Realm Name -- A resolvable AD realm. It's essential to have correct DNS configuration for the resolution to work. If the AD server is the sole DNS server and is configured automatically(via DHCP) or manually during network interface configuration, it should work fine. If needed, DNS servers for a network connection can be set from System -> Network Interfaces screen.
- Administrator Username -- Administrator username to be used for authentication while joining AD.
- Password -- Password for the above user.
That’s it. SSSD simplifies many other parameters required by previous method. Going forward, we may have to include some advanced input depending on AD infrastructure of a given scenario. I look forward to community members that are experienced with AD to chip in.
##Configuration save
Upon submitting the form in the UI, the following happens.
- If NTP service is not running, the config is rejected as it’s essential for AD integration to work properly.
- config is also rejected If the provided Domain/Realm cannot be resolved. In this case the user is advised to verify DNS configuration and input before trying again.
- The domain controller is “discovered” with this command
realm discover --name-only <domain>. Again, config is rejected if discovery fails.
Once the config is verified as indicated above, it’s saved. Note that username/password are not verified yet.
##Service switch on
When the service is switched on, an attempt is made to join AD using the credentials saved in the config. Just like during configuration save, NTP and domain name resolution are verified. Finally, join is attempted with this command realm join <domain>. Any low level errors are bubbled up and presented on the Web-UI after some elaboration for clarity.
Active Directory service being on means that the Rockstor system has joined Active Directory. But the domain user/group information is not listed anywhere in the Web-UI.
##Service switch off
This is a simple realm leave command.
##How is this tested by Rockstor team?
All AD related code is tested with Samba 4 Domain Controller which is compatible with Active Directory. I am hoping that AD users in the community will come forward and help us improve this feature as needed.
##Where to from here?
RHEL 7 documentation and other sources on the internet provide excellent documentation but also make it clear there is no universal AD integration for all. So instead of over engineering it, it’s best if users try to integrate their Rockstor systems with AD and point out shortcomings and nice to have extensions. For example, how should Samba service configuration be updated for AD integration? or if we should enumerate domain users/groups and show them on the Web-UI and support certain features like ACLs.